October 31, 2018

Last week was another exciting opportunity for collaborators and contributors to solve identity issues together at the Internet Identity Workshop (IIW). A team from Sovrin attending IIW was delighted to note that a lot of the talks focused on self-sovereign identity, related systems and the technology in development to make it a reality.
For those who have not attended, IIW is a little different from other conferences. At its heart, IIW is highly participatory. The workshop actually describes itself as an ‘un-conference’ because it has no predetermined keynotes or panels. It’s about getting stuff done.
At the beginning of each day, anyone who would like to conduct a session takes a sheet of paper and writes a session title on it. Then those who have a session introduce what they want to discuss later in the day. Once everyone has introduced their session they post it on the agenda wall in one of the hourly time slots. After all the sessions are in place, anyone may choose to go to any session.
At this meeting of IIW, Sovrin hosted a session offering a live demo of our network. While we introduced the structure of the demo in our session, we gave attendees the opportunity to complete it throughout the entirety of the conference. The purpose of this demo was to show how to combine attributes from multiple credentials to create a trusted proof using self-sovereign identity on the Sovrin Network.
Demo Overview
The demo was really pretty simple. Attendees were challenged to receive and combine two verifiable credentials to prove they were at IIW this year before the end of the conference. To prove attendance, we asked them to verify three pieces of information: their name, organization, and whether they were a human or a dog. The last attribute was inspired by Phil Windley’s favorite New Yorker comic.

Three representatives of the Sovrin Foundation represented credential issuers and responsible for issuing the credentials that attested these different attributes about the attendees. No single issuer could attest to all three attributes, but a combination of two credentials from separate issuers would give the attendee all three attributes. These issuers were wearing either a blue, green, and yellow tropical lei throughout the conference.

Once attendees had at least two credentials from different issuers, they could prove they were at IIW by interacting with our verifier, who wore a red garland. The verifier requested the required three attributes from the attendees: name, organization, and whether they were a human or a dog.

This example illustrated the power of multi-sourced identity. Because each attendee was not tied to just one person for their entire identity, they could easily collect credentials that attested information about themselves and combine that information in unique ways to prove claims about themselves. In this case, the credentials and attributes interacted like a Venn diagram.

Technology
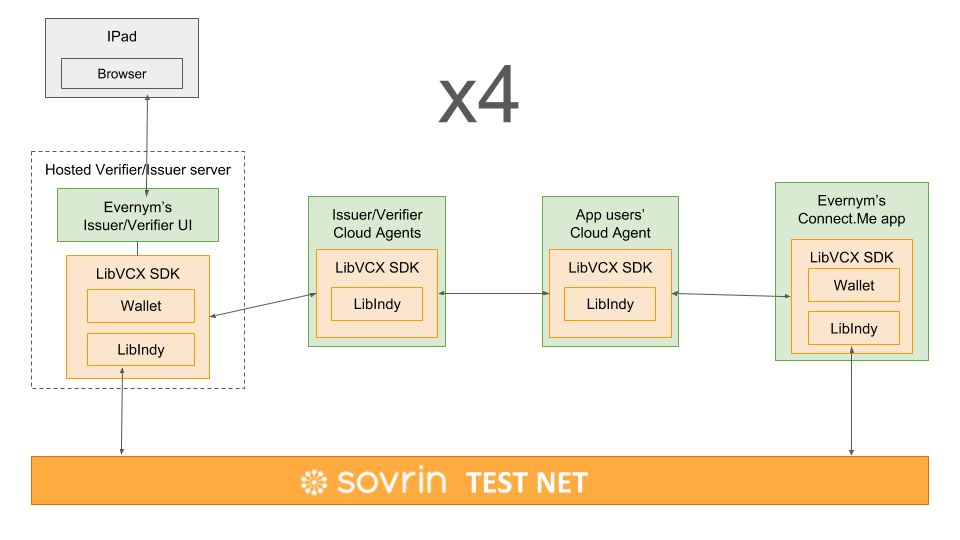
While we have been building a reference agent in the Hyperledger Indy-Agent repository, for this demo we used Evernym’s Connect.Me app which built on the same Indy-SDK but has a much more flexible user interface. Attendees downloaded a beta version of Connect.Me to store their credentials. We created four enterprise agents and controlled them using iPads while at the conference. Below is a more simple architectural diagram for the technically curious. For future demos we hope to begin using more robust open source solutions as we build them throughout the Sovrin community.
Outcome
70 people completed the demo at IIW, and got a small prize from Sovrin in return. Over 100 people at IIW downloaded the app and received at least one verifiable credential. The demo successfully showed a simple example of the power of Sovrin as an identity solution, especially with multi-sourced identity. If you did not get the chance to try the demo, we may continue to present it at upcoming hackathons and meetups.
IIW was a great experience for us at Sovrin. Collaboration with the other exemplary organizations in this space has been critical as we define protocols and standards around self-sovereign identity for the future of the internet. During this conference we were able to learn from what other identity solutions are doing and offer some of our own insight into what truly works. Moving forward, we’re excited to continue collaborating to develop self-sovereign identity into its fullest potential.
« “Identity for Good” program helps provide SSI to NGOs and nonprofits Announcing public review of the Sovrin Governance Framework V2 »